ePIF – Citic Pacific Mining
A reactive web app within the OutSystems platform. the ePIF provides process workflow and automation over a purchase request permissions process.
Filter by Category
Filter by Author
A reactive web app within the OutSystems platform. the ePIF provides process workflow and automation over a purchase request permissions process.
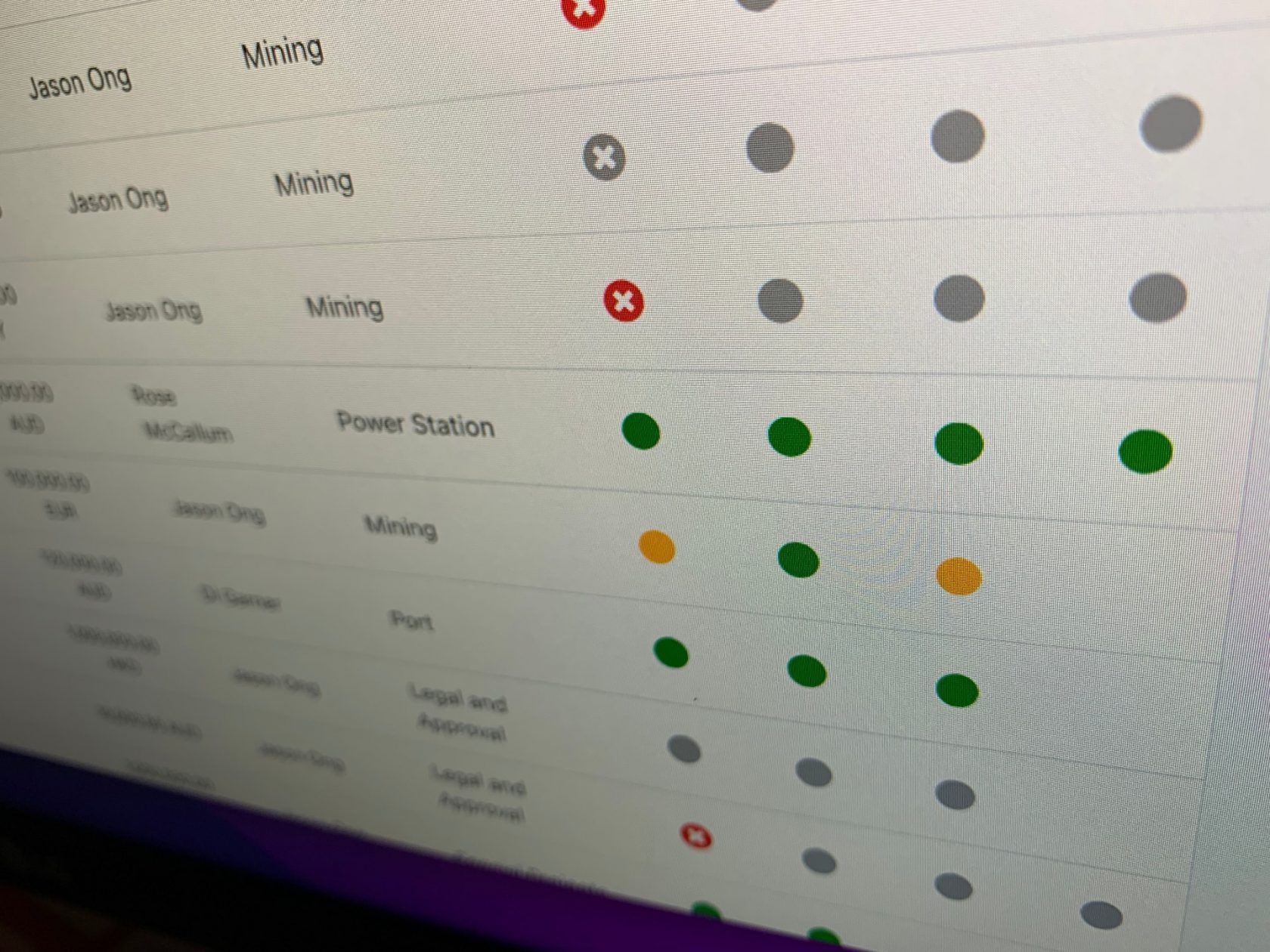
The internal tool, app integrates multiple data sources into a fit for purpose workflow process for staff to create and follow purchase requests. On submission of a request, the department head is notified of a requirement to review and approve or reject. Approval notifies the next required authorisation in the chain. Rejection ends the process and notifies the requestor. Approvals the overall request are timeframe restricted with the request expiring if the approvals are not all resolved.
Requests were submitted to the purchasing department via a downloaded and printed out word document. once submitted, there was a high onus on the purchasing officers to process the forms, seeking confirmation and approval from relevant and responsible parties.
Digitising the physical forms and adding an automated business process management workflow Progress tracking, repeatability and distribution of workload to responsible parties improves FTE staff utilisation and inherent monitoring and notification ensures better quality control.
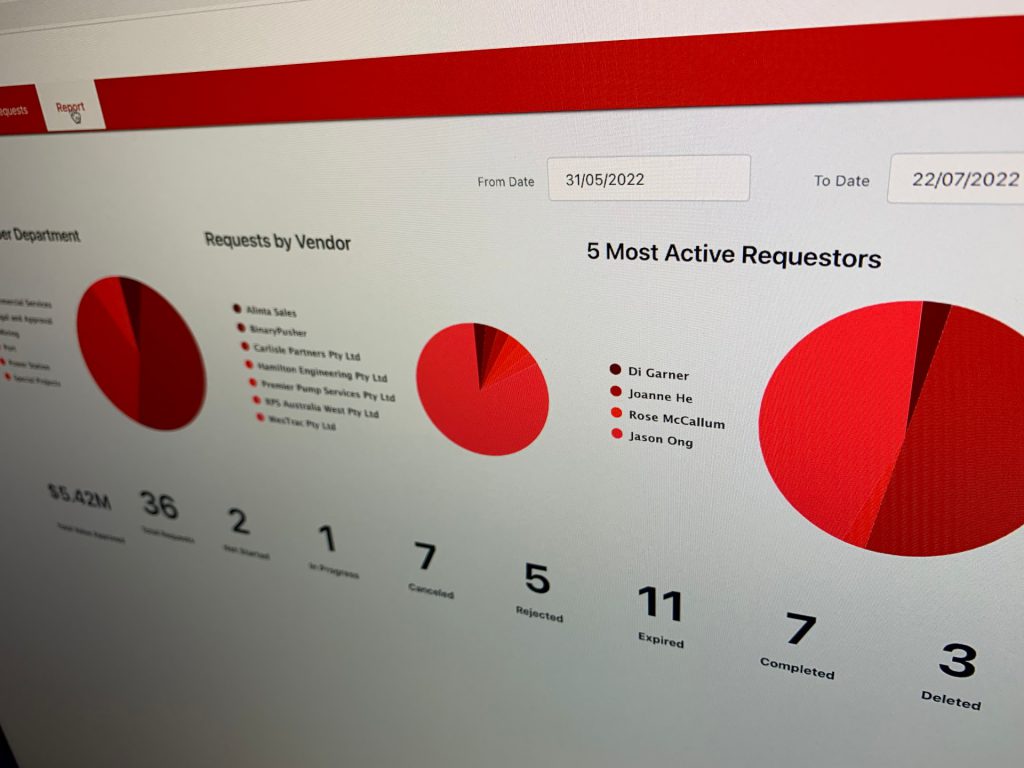
Reports uses the standard OutSystems Charts module along with advanced SQL queries to generate pivotal data. Additional options to search and filter the report data has been developed but not enabled in the final release.
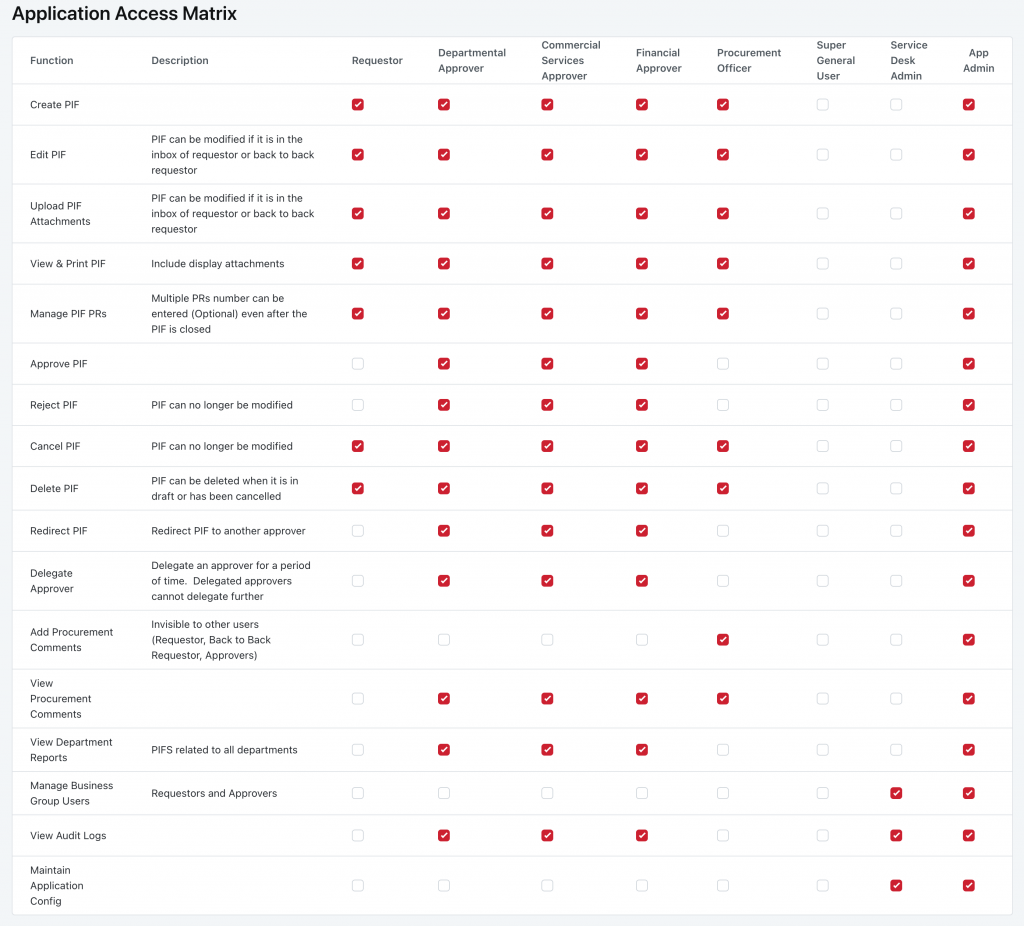
Granular permissions re assigned to application roles via an application role and functionality matrix. Functions and Roles are dynamic elements within the system, so adding or removing roles or Functions will automatically provide a Role x Function matrix configuration point.
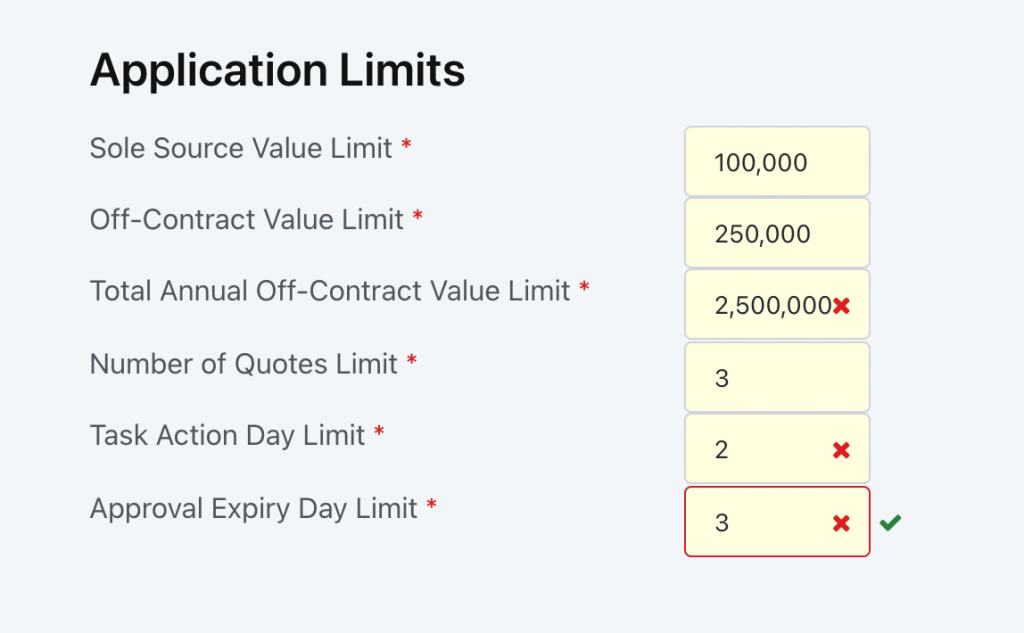
Application limits can be overridden by any user configured with the app administrator role. core application limits are shown without any associated icons. overridden values are shown with ‘x’ allowing an administrator to cancel the override. newly entered overrides show a ‘x’ and tick allowing the administrator to complete or cancel an override. Data integrity is preserved on existing requests such that previous requests hold a snapshot of the application limits at the time. New requests will be processed according to the overridden rule limits.